Reduce Risk Across Your Software Supply Chain
Your security does not end at your codebase. Every vendor, supplier, and service provider you rely on expands your attack surface. Manifest gives you the visibility and workflows to assess supplier security posture, exchange SBOMs, monitor vulnerabilities, and enforce C-SCRM best practices, all within a unified platform.
Traditional vendor security focuses only on questionnaires and point-in-time reviews. C-SCRM goes further by ensuring cyber risks across hardware, software, cloud, and service providers are continuously identified, monitored, and controlled. Manifest operationalizes this approach so you can reduce third-party risk and protect your software supply chain end-to-end.
Outcomes of Stronger C-SCRM
Gain continuous visibility into vendor vulnerabilities and dependencies, lowering the risk of hidden threats from your suppliers.
Meet NIST C-SCRM, DoD, and CISA requirements with a structured, proactive approach to supplier risk management.
Protect business continuity by detecting and mitigating supply chain risks before they disrupt critical systems.
Demonstrate supply chain security assurance in procurement processes, winning confidence with stakeholders and accelerating relationships.
How Manifest Empowers C-SCRM
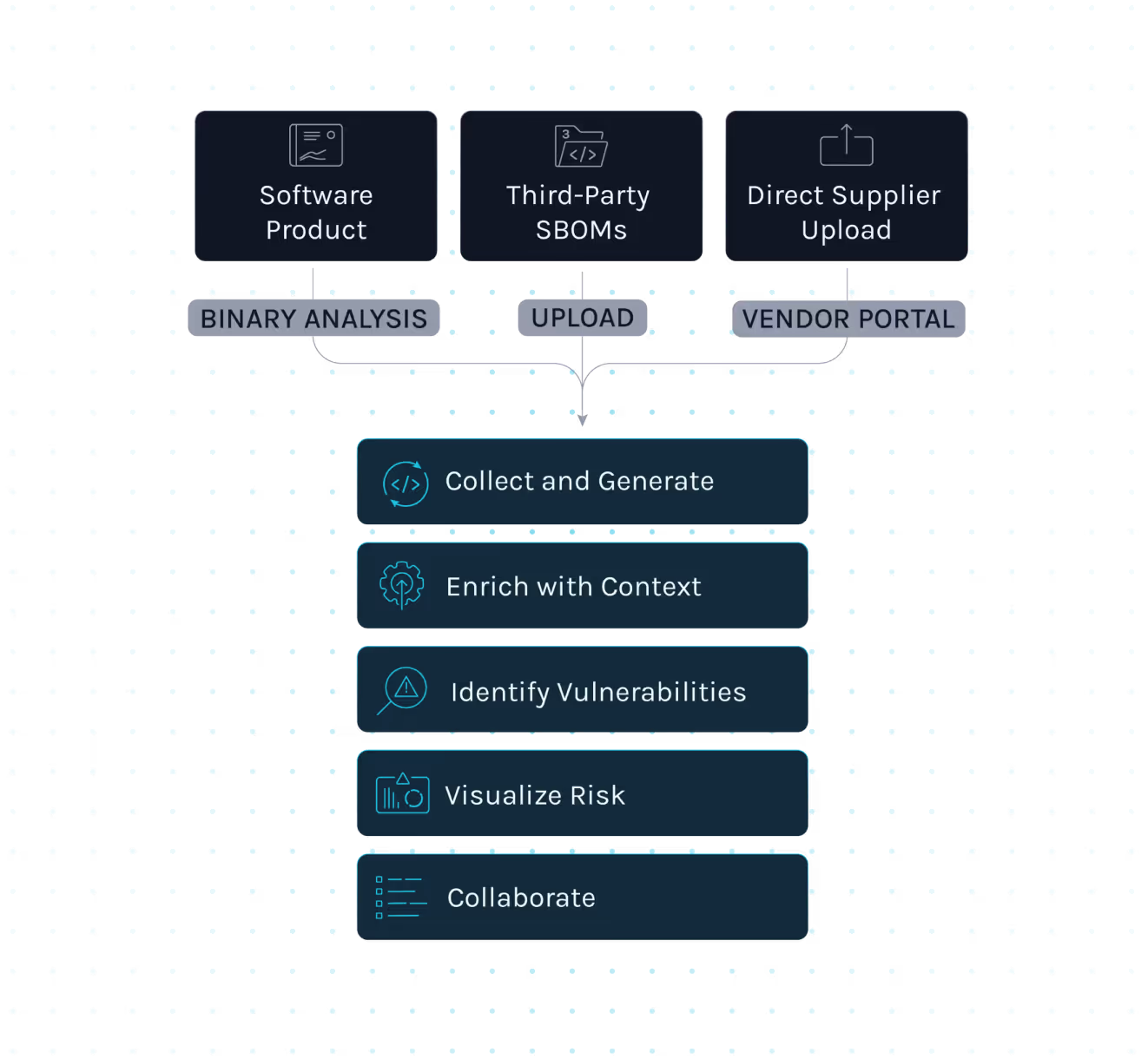
- Vendor SBOM Exchange
Request and manage SBOMs from vendors to validate components and dependencies.
- Supplier Risk Scoring
Rate vendors by vulnerability exposure, compliance status, and exploitability context.
- Continuous Monitoring
Track vendor vulnerabilities and automatically flag new risks as they emerge.
- C-SCRM Alignment
Map your vendor program to NIST, CISA, DoD, and ISO/IEC C-SCRM best practices.
FAQs
A Software Bill of Materials (SBOM) is a detailed inventory of every component inside your software, including open-source libraries, dependencies, and third-party code. It helps you identify hidden vulnerabilities, manage licensing risk, and comply with regulations like EO 14028 and NIST 800-218.
Manifest automates SBOM generation across your entire application fleet, in seconds. We support formats like SPDX, CycloneDX, and VEX, and go beyond repositories to analyze binaries, embedded code, and real-world deployments.
Traditional Software Composition Analysis (SCA) tools scan individual repos and often generate noisy alerts. Manifest offers universal technology transparency, assessing risk across your entire product line, including non-CVE threats, committer insights, and AI models.
SBOMs should be generated continuously, not just when a product is released. Manifest supports real-time SBOM monitoring, enrichment, and vulnerability tracking so your inventory stays accurate, actionable, and audit-ready.