Lessons from Manifest’s Assessment
A newly disclosed critical vulnerability (CVE-2025-7783) in the widely used JavaScript form-data library poses a significant risk to millions of applications. This flaw allows attackers to exploit predictable boundary values in multipart form uploads, potentially leading to parameter injection attacks and, in some cases, remote code execution.
Immediate Remediation Steps
Organizations using the form-data library should take the following actions:
- Upgrade to a patched version
- If using v4.x, upgrade to 4.0.4
- If using v3.x, upgrade to 3.0.4
If using v2.x, upgrade to 2.5.4
- Review application exposure
- Identify where the vulnerable versions are used, especially in components that handle multipart form uploads with user-controlled data.
- Check if your applications leak Math.random() outputs, which can enable boundary prediction.
- Harden request handling
- Ensure backend systems properly sanitize and validate parameters to reduce the risk of injection.
- Ensure backend systems properly sanitize and validate parameters to reduce the risk of injection.
Understanding the Vulnerability
The issue arises from the use of JavaScript’s non-cryptographic Math.random() function to generate multipart boundary values. This predictable randomness allows attackers to infer future boundary values by observing sequential outputs, enabling them to craft malicious payloads that bypass input sanitization.
The vulnerability affects:
- Versions <2.5.4,
- Versions 3.0.0–3.0.3,
- Versions 4.0.0–4.0.3.
This flaw mirrors patterns seen in other recent PRNG-based vulnerabilities, such as the one in the undici HTTP client library, highlighting a broader issue with predictable randomization in security-sensitive contexts.
Why This Vulnerability Matters for JavaScript Users
JavaScript is the world’s third most widely adopted programming language, with 13 million tracked customers globally according to Radixweb. It underpins countless modern web applications and frameworks. Popular JavaScript technologies include jQuery, Google Tag Manager, Bootstrap, Modernizr, jQuery UI, Stick, Masonry, and React.js, many of which integrate or indirectly rely on form-data functionality for handling file uploads and form submissions.
Given this widespread usage, there is wide exposure. Manifest’s analysis identified that 86% of sampled customers and prospects had some degree of exposure to CVE-2025-7783. The impacted assets, built and bought software, ranged from as few as 1 to as many as 3,000+ per organization.
Manifest’s Response: Proactive Assessment and Notifications
As soon as details of CVE-2025-7783 were released, Manifest immediately mobilized its security team to assess customer environments. Our analysts worked through the last few days, leveraging our platform’s data visibility to quickly identify where vulnerable versions of the form-data library were in use.
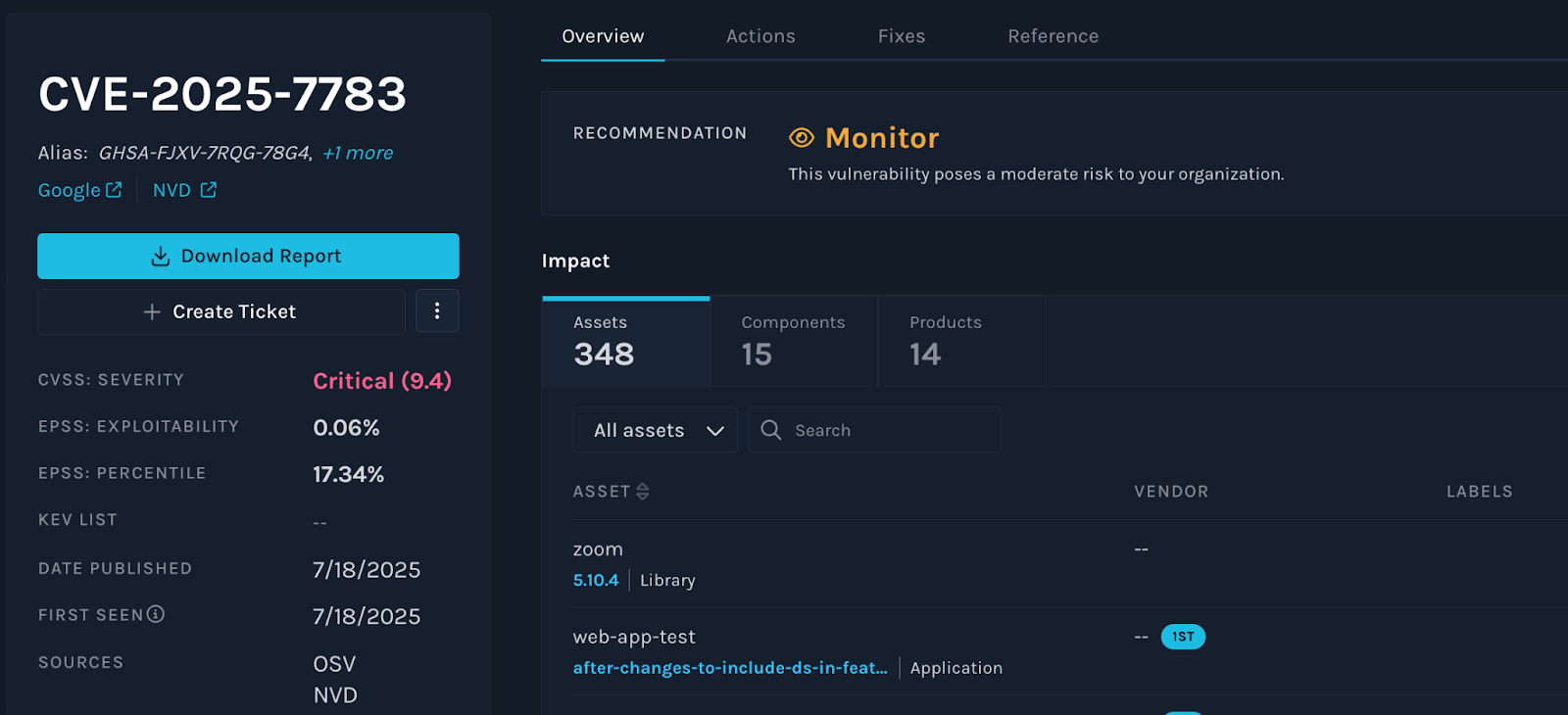
Within hours, we began notifying customers of their specific exposure levels, including the affected assets and guidance on urgent remediation steps. This rapid response ensured that organizations could take decisive action, leveraging the Manifest Platform data to inform and contextualize incident response.
Manifest recommends that customers monitor this vulnerability; however, there is no need to reprioritize existing patching plans. Although the CVE has been assigned a CVSS score of 9.4, it currently has a low exploitability score from EPSS. Exploitation at scale is hindered by several factors, as attackers would need multiple conditions to align precisely (such as leaking random values, controlling input, and targeting a vulnerable backend), making it difficult to execute in practice. Organizations should upgrade their data-form libraries as recommended.
Why Identifying Exposure is Often the Hardest Part
While patches are available, the challenge for most organizations is knowing exactly where the vulnerable code is running. Modern applications rely on extensive dependency chains, and the form-data library may be buried deep within other packages.
This is where Software Bills of Materials (SBOMs) become invaluable. SBOMs provide a complete inventory of the open-source components in use, including their versions and relationships. With an SBOM:
- You can quickly query whether affected versions of form-data are in your environment.
- You can prioritize remediation for systems that are most at risk.
- You can streamline communication with developers and vendors to ensure patches are applied consistently.
The Bottom Line
CVE-2025-7783 this is the latest in a long line of software supply chain vulns, from Apache struts to log4shell to XZ utils, rendering the need for dependency management mission critical. In a JavaScript ecosystem powering millions of applications worldwide, visibility into dependencies is no longer optional, it’s essential.
By leveraging SBOMs as part of your vulnerability management strategy, you can move from reactive firefighting to proactive defense, reducing the time from advisory to remediation when every second counts.
Stay ahead of threats. With the right data at your fingertips, vulnerabilities like CVE-2025-7783 become challenges you can address swiftly, not crises that catch you off guard. Prepare for the next software supply chain vulnerability, schedule time with the Manifest team.



