What is Vulnerability Management?
Vulnerability Management is the continuous process of identifying, prioritizing, and remediating security flaws across software and supply chains.
Manifest redefines this process by making it smarter, automated, and actionable, giving teams clarity on what to fix first, not just a long list of CVEs.
Why Smarter Prioritization is Key
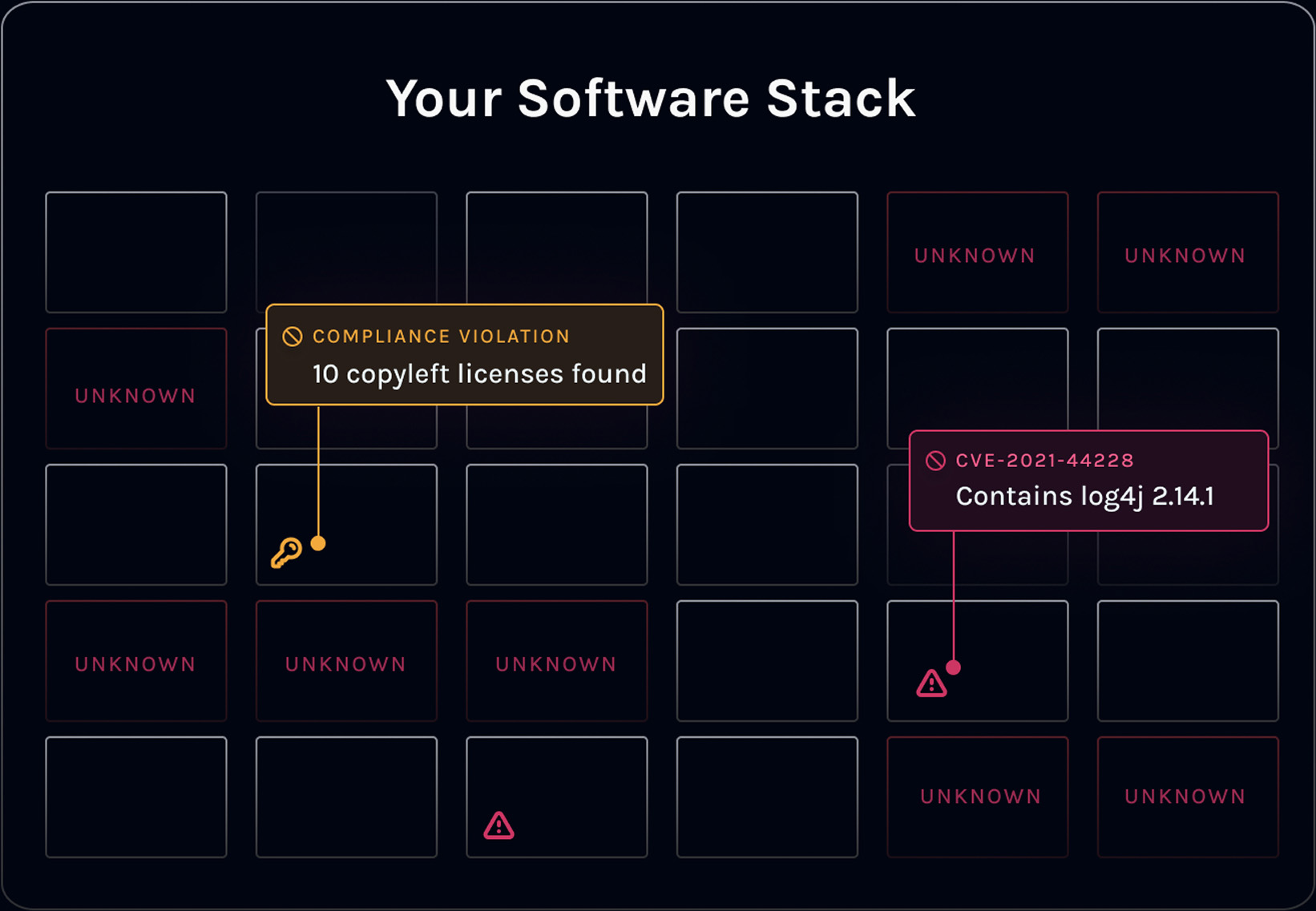
Too many alerts, too little clarity. Traditional vulnerability scanning leaves teams buried under false positives and low-priority issues. Manifest changes this with:
Determine if a vulnerability is actually reachable in your code before escalating.
Rank vulnerabilities by exploitability (KEV, EPSS) and business criticality, not just CVSS severity.
Prioritize and triage directly in Manifest or push prioritized tasks into Jira, ServiceNow, or other tools.
The Challenges of Traditional Vulnerability Management Workflows
Even with SBOM data, most workflows fail because:
CVSS-only scoring inflates noise.
Manual triage inflates noise.
Communication with stakeholders is slow.
Teams can't track what's fixed, ignored, or mitigated.
How Manifest Empowers Stronger Vulnerability Management Programs
FAQs
Manifest goes beyond CVSS scores. We enrich vulnerabilities with Known Exploited Vulnerability (KEV) data, Exploit Prediction Scoring System (EPSS) probabilities, and business criticality. Combined with reachability analysis, this creates a clear, risk-based priority list for faster remediation.
Yes, Manifest supports AI/ML vulnerability management. Through our AIBOM (AI Bill of Materials) framework, Manifest extends vulnerability management into the AI supply chain — helping you track and prioritize risks in datasets, models, and AI components alongside traditional software dependencies.
Manifest is designed to fit into your existing ecosystem. Vulnerabilities can be triaged and prioritized directly in the platform, or pushed into tools like Jira, ServiceNow, or Slack so remediation teams work in the systems they already use.