Identify and Resolve Supply Chain Risks, Fast
Supply chain threats are growing. Manifest Product Security helps you stay ahead by identifying and resolving risks before they impact your customers, compliance, or business velocity.
Manifest Product Security integrates early in the software development life cycle (SDLC) to support continuous innovation, securely.
Gain deep visibility into your product builds
Model and track risks as they evolve
Detect vulnerabilities early
Automate remediation to ensure continuous compliance
Blind Spots in your Software Supply Chain
- They scan individual repos, not full product systems
- They generate noisy, low-context alerts
- They don’t provide a clear path to resolution
What you can do with Manifest Product Security
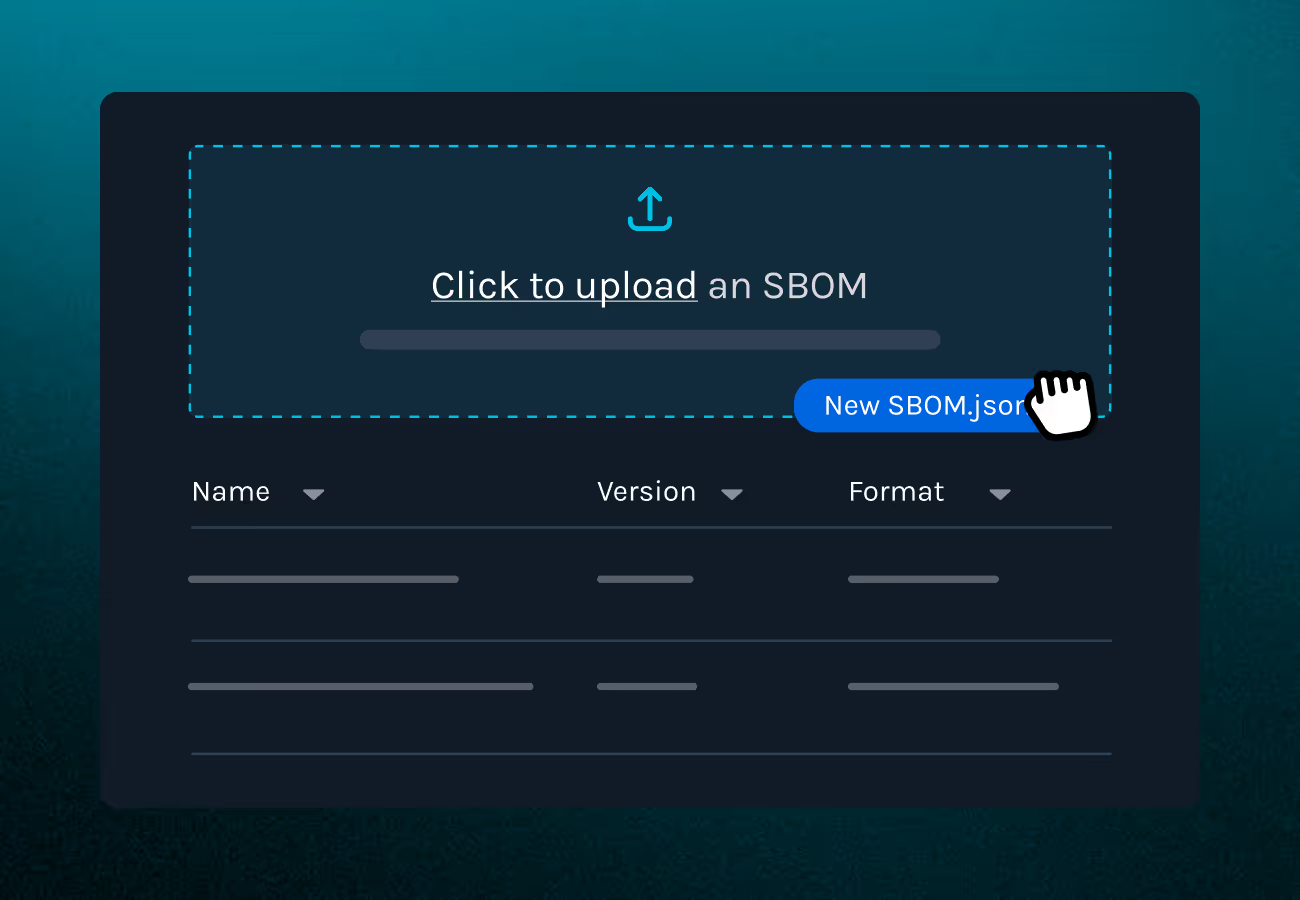
Validate, enrich, generate, and securely share your software transparency data. Upload SBOMs in CycloneDX or SPDX formats, Product Security automatically validates them, heals format issues, and fills in missing metadata. Generate VEX documents in CSAF or OpenVEX to provide context around vulnerabilities, and ingest VEX from vendors to triage risk effectively.
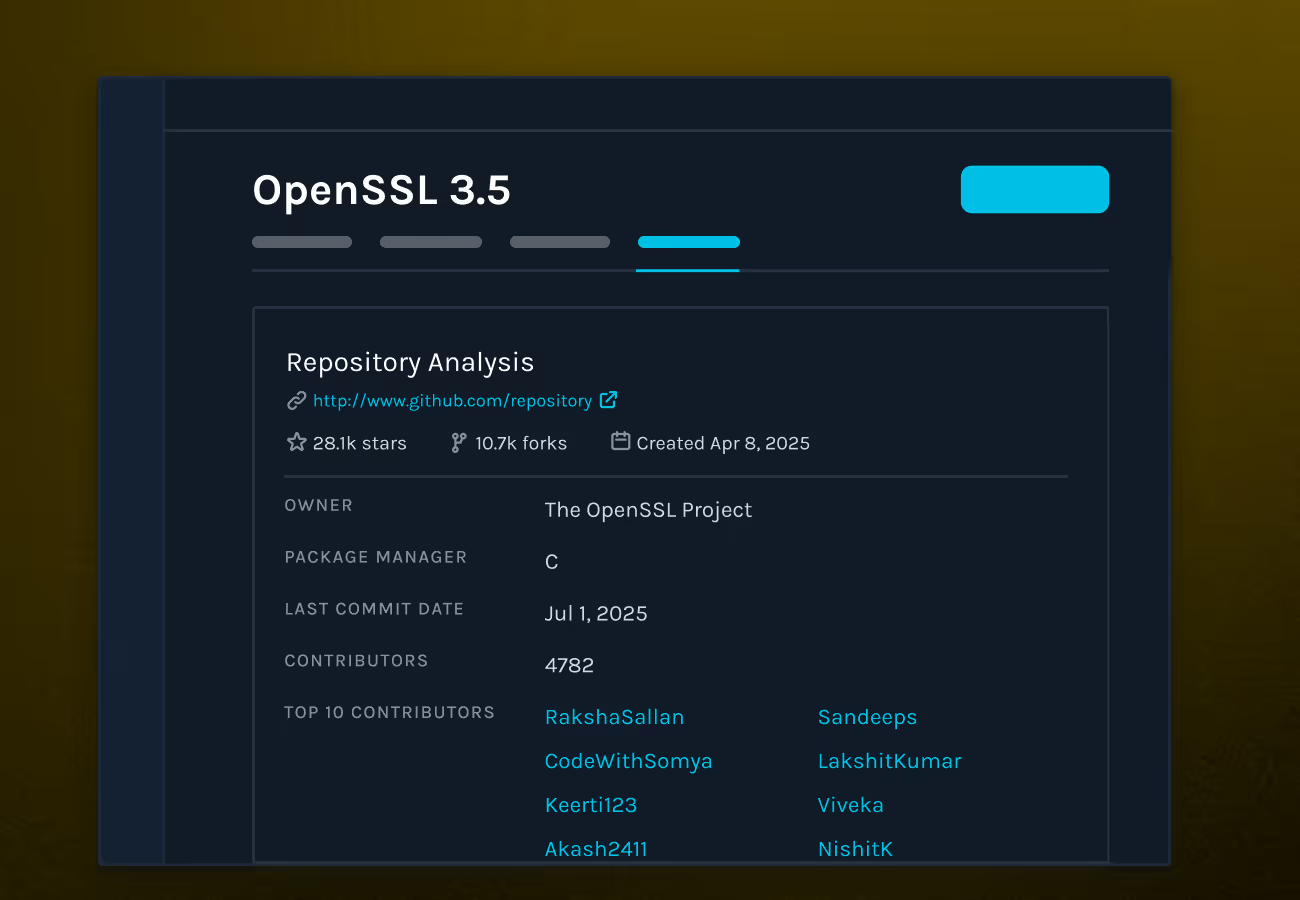
Assess open-source components directly from GitHub. With a single URL, analyze the security and license risks of third-party code before it enters your build process, so you can stop risky components at the gate.
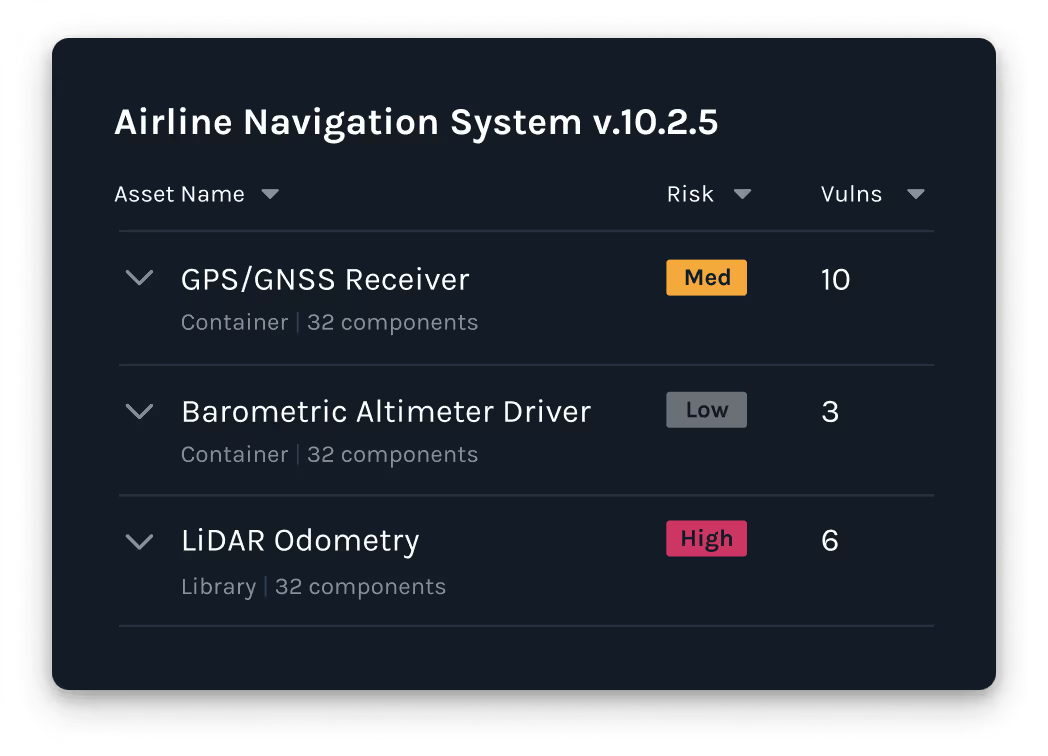
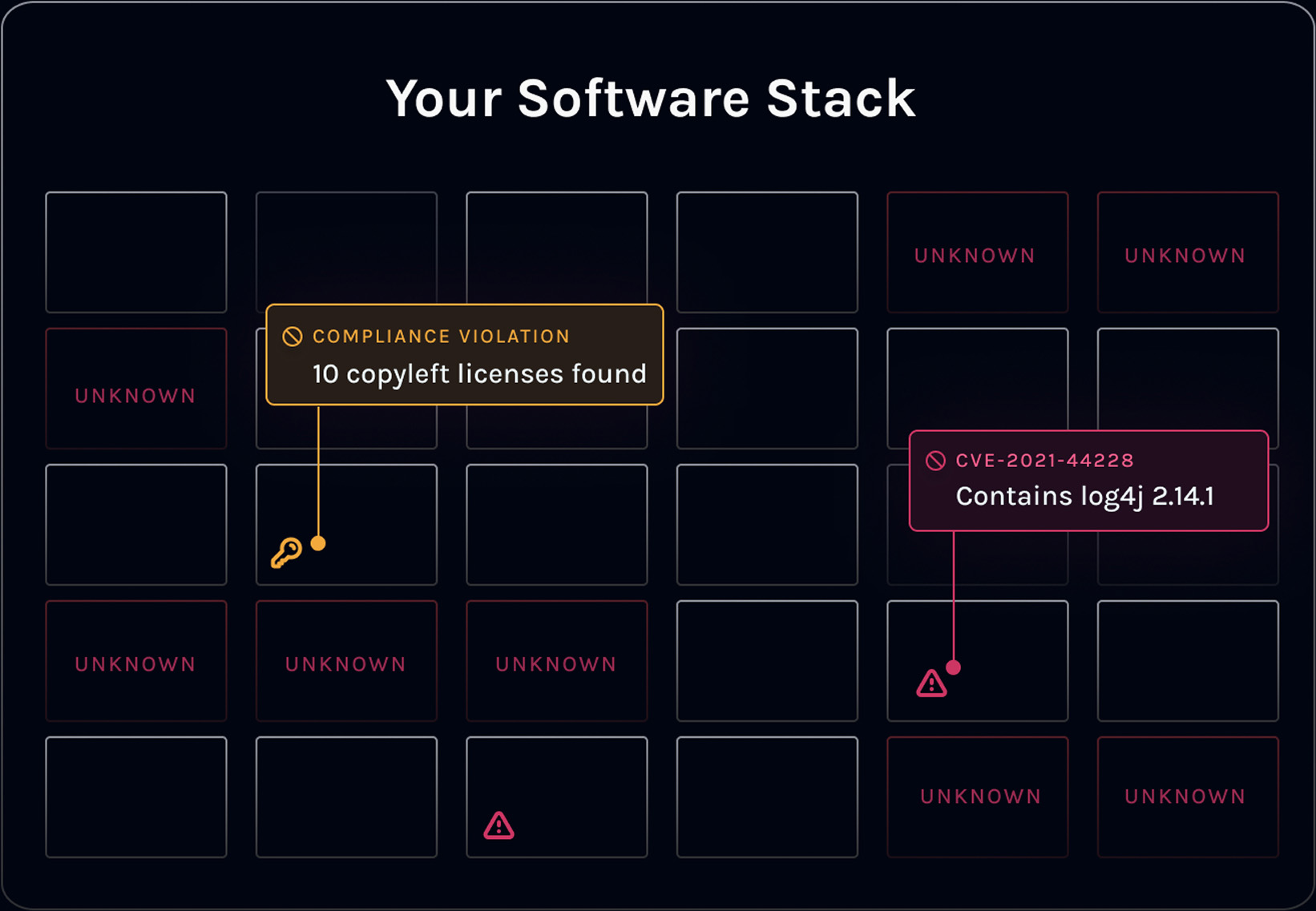
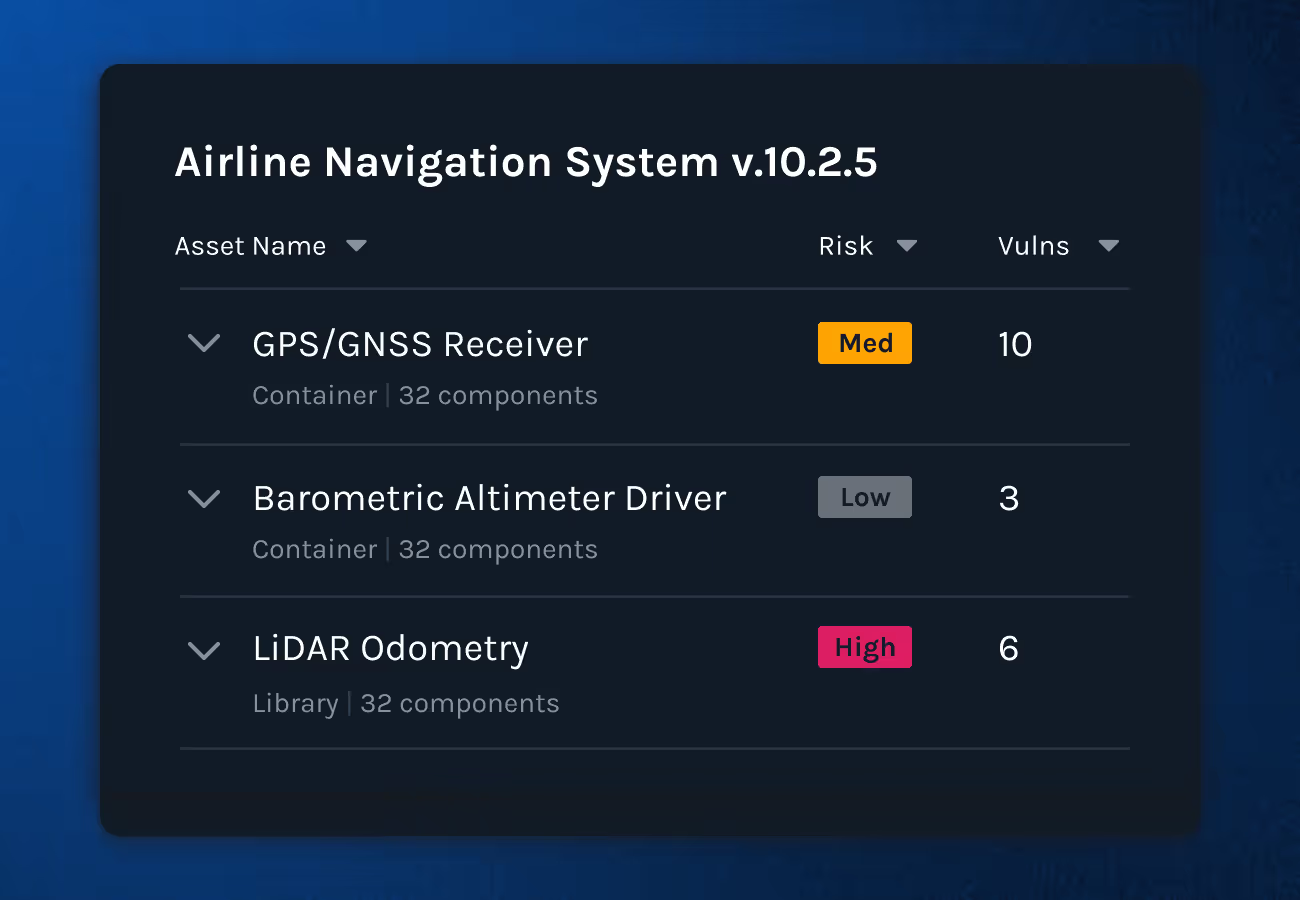
See the full picture of your software stack. Map every product, related asset, and underlying component. Product Security provides an intuitive view of all software components and their associated vulnerabilities, no more guessing what's running in production and which products are impacted.
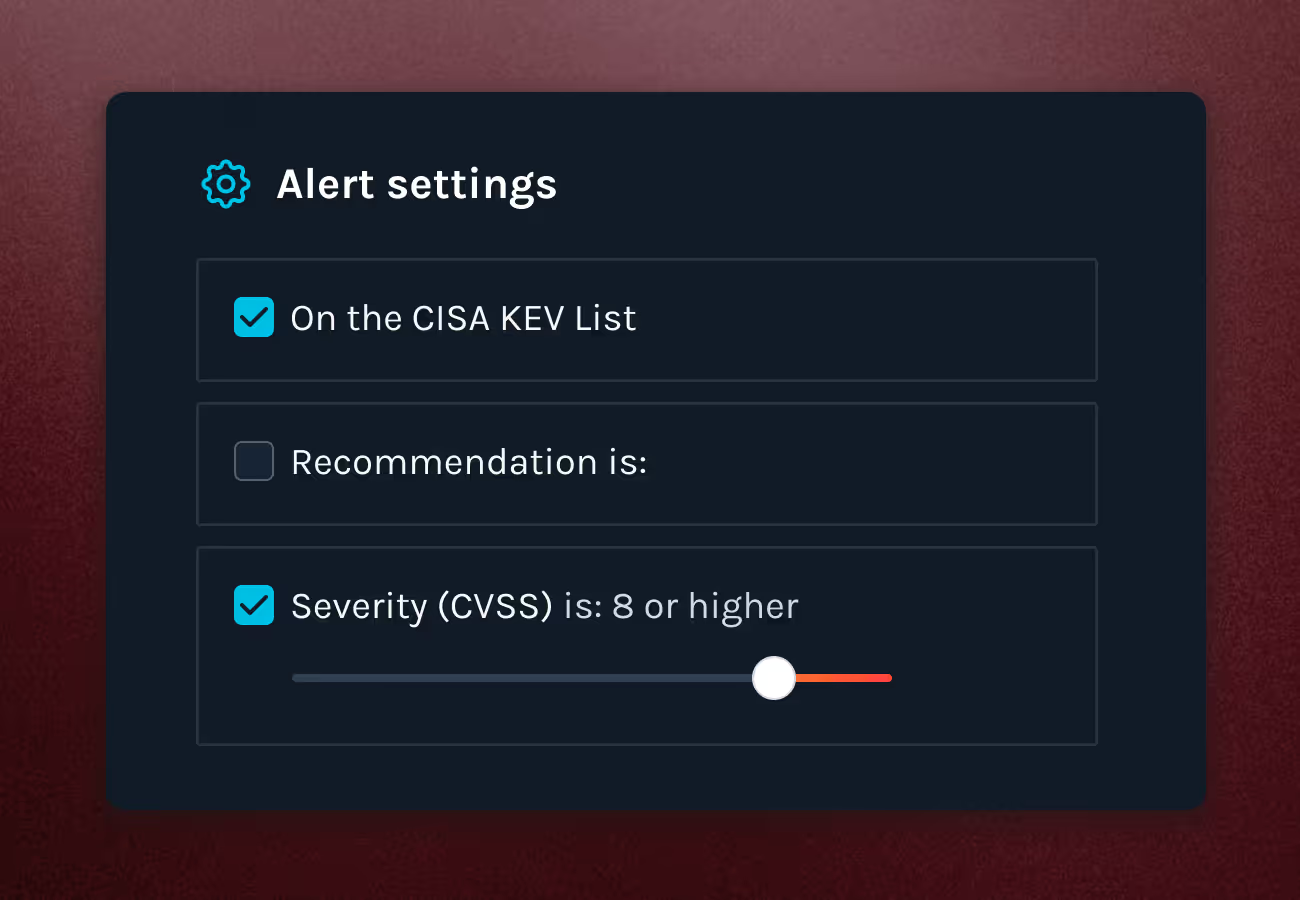
Cut through the noise with targeted alerting. Set your own thresholds and receive alerts based on:
CISA Known Exploited Vulnerabilities (KEV)
CVSS v3/v4EPSS (Exploit Prediction Scoring System)
Manifest-recommended actions
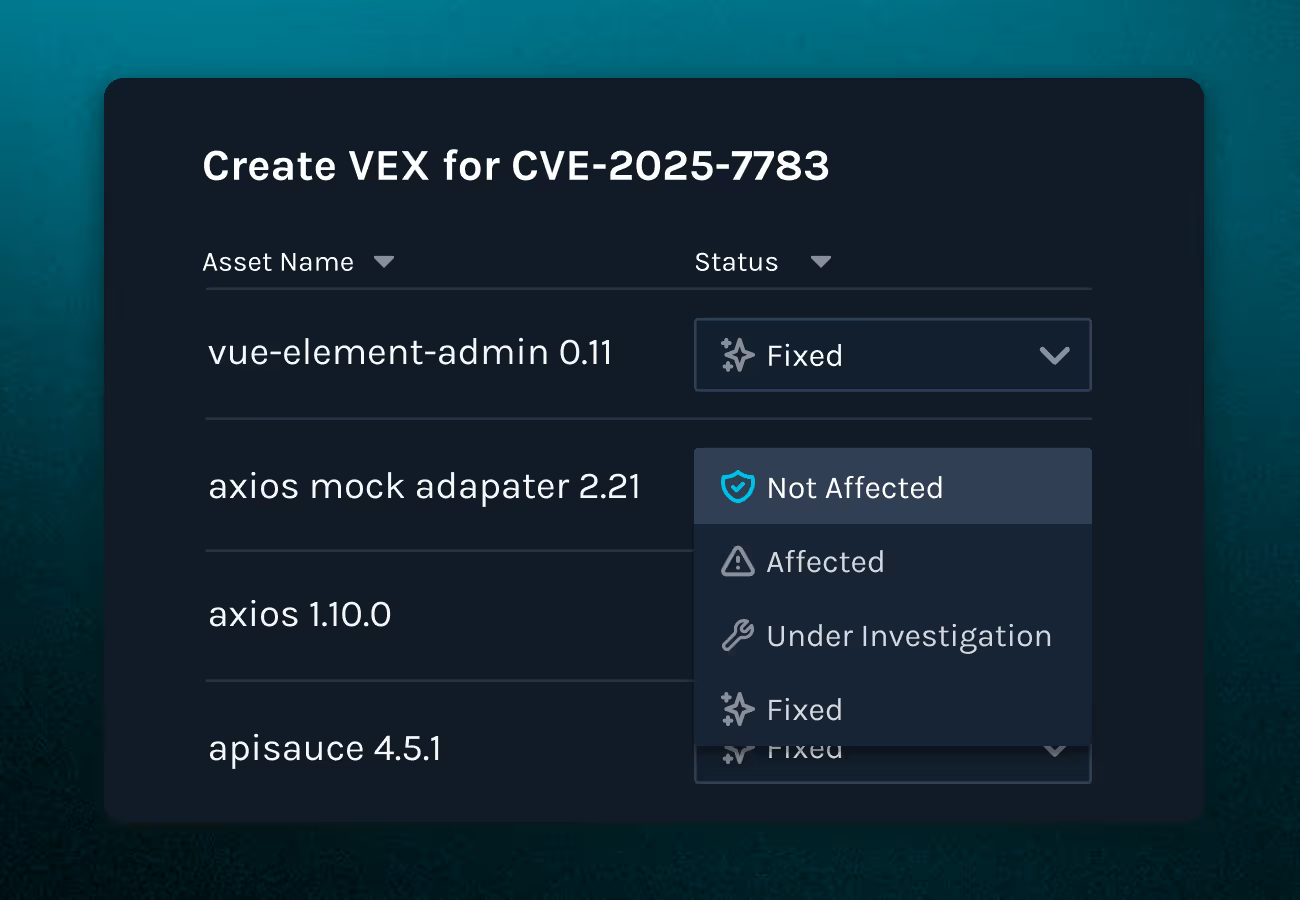
Communicate risk and compliance confidently. Share SBOMs and VEX documents with customers, partners, and regulators in a secure, scalable way. Manifest helps you prove due diligence without increasing your team’s workload.
FAQs
SBOM (Software Bill of Materials) management refers to the process of generating, validating, updating, and sharing an inventory of all software components in a product. Software is the only thing we buy that we don’t have a list of ingredients or safety tests for. SBOMs enable visibility, vulnerability detection, and compliance across the software supply chain. With proper SBOM management, organizations can identify risks before they affect customers or operations.
Manifest Product Security offers a real-time view into your entire software supply chain, enabling early detection of vulnerabilities, license violations, and misconfigurations. It integrates SBOM and VEX support, automates exposure reports, and helps streamline incident response, making your software more secure without slowing development.
VEX (Vulnerability Exploitability Exchange) documents provide context about whether a known vulnerability in a component actually affects your software. Manifest allows you to generate VEX in CSAF or OpenVEX formats and ingest VEX from third-party vendors, helping you prioritize what truly needs remediation.
Manifest integrates at multiple stages of the SDLC to provide real-time risk visibility and policy enforcement. We recommend customers implement Manifest at the start of the SDLC, when open-source software (OSS) and third-party software are being evaluated for use. Manifest enables developers to upload SBOMs, receive alerts on vulnerable components, and assess open-source code before use, supporting secure development without sacrificing speed.
Manifest automates SBOM validation, generates VEX, and allows secure sharing of artifacts with regulators and partners. This simplifies compliance with standards from CISA, NTIA, FDA, the EU and other regulatory bodies, reducing manual effort and demonstrating maturity in your software assurance program.