Why Government Suppliers Must Rethink Software Supply Chains
That is where Foreign Ownership, Control, or Influence (FOCI), enters the conversation. Historically, FOCI lived in the world of facility clearances, board structures, and corporate oversight. But the modern defense industrial base does not run on steel and circuitry alone. It runs on open-source libraries, container images, build pipelines, and AI models. That means FOCI has expanded into the software and digital supply chain, whether we like it or not.
This matters to every defense contractor and increasingly to any company working with U.S. government customers. The government’s direction is clear. Supply chain security is no longer a paper compliance exercise. It is becoming a continuous, evidence-based expectation, especially as adversarial nations treat software ecosystems as a strategic battleground.
FOCI must be seamlessly integrated into how open source software is evaluated, selected and continuously monitored to prevent foreign influence over mission critical systems.
Why This Is Happening Now
In hindsight, this evolution was inevitable. Recent Executive Orders elevated software supply chain security to a government-wide priority and directed NIST to publish guidance on software supply chain risk management. The result is a more formal expectation that agencies and their suppliers can prove they are building software securely.
And while policy tends to move slowly, adversaries do not. The last few years have shown exactly how software supply chains can be manipulated, not only with vulnerabilities, but with influence.
FOCI is the policy language for a broader reality. Software risk is not just about vulnerabilities anymore. It is about control, authorship, and provenance.
FOCI Risk: Not Just a Corporate Structure Problem
FOCI is formally defined by the U.S. government as the ability of a foreign interest to direct or influence a company’s management or operations in ways that can risk national security. That definition is well established in DCSA guidance and in federal regulations.
But here is the twist. Modern software is not owned in the traditional sense. It is assembled, compiled, and shipped at machine speed. Increasingly, it moves in container images that flow through CI/CD pipelines and land in the fleets that run critical infrastructure, from fighter jets to cars to the systems that keep power and logistics moving.
A single application can contain thousands of third-party components maintained by a multitude of individuals across the globe. Some of those maintainers may live in countries where governments have extraordinary powers to compel cooperation. Others may operate under legal regimes that make silent influence possible and difficult to detect.
Even if your company is perfectly clean from a corporate standpoint, your dependencies might not be.
That is why FOCI is becoming everyone’s problem. It is less about company ownership, employees, and subcontractors, and more about the supply chain, specifically who can effectively influence your software through the dependencies, maintainers, and build systems you rely on.
The Risk Is Real, and It Has Already Happened
Supply chain risk is not hypothetical. We have already watched the playbook unfold in public.
The xz-utils backdoor in 2024 is a striking example of what modern influence looks like. A sophisticated adversary did not hack xz-utils in the traditional way. They infiltrated the project socially, built credibility over time, and inserted malicious code into upstream releases. The vulnerability, tracked as CVE-2024-3094, carried a CVSS score of 10 and prompted urgent guidance to downgrade affected versions.
If xz-utils demonstrated long-term infiltration, the polyfill.io incident demonstrated something equally sobering. Central points of trust become ideal choke points. When researchers disclosed a supply chain compromise impacting the polyfill.io domain, the blast radius was immense. Hundreds of thousands of sites were reportedly embedding the script.
These are not just security incidents. They are warnings about the fragility of the software ecosystem and how easily critical infrastructure can inherit risk from code controlled by adversaries.
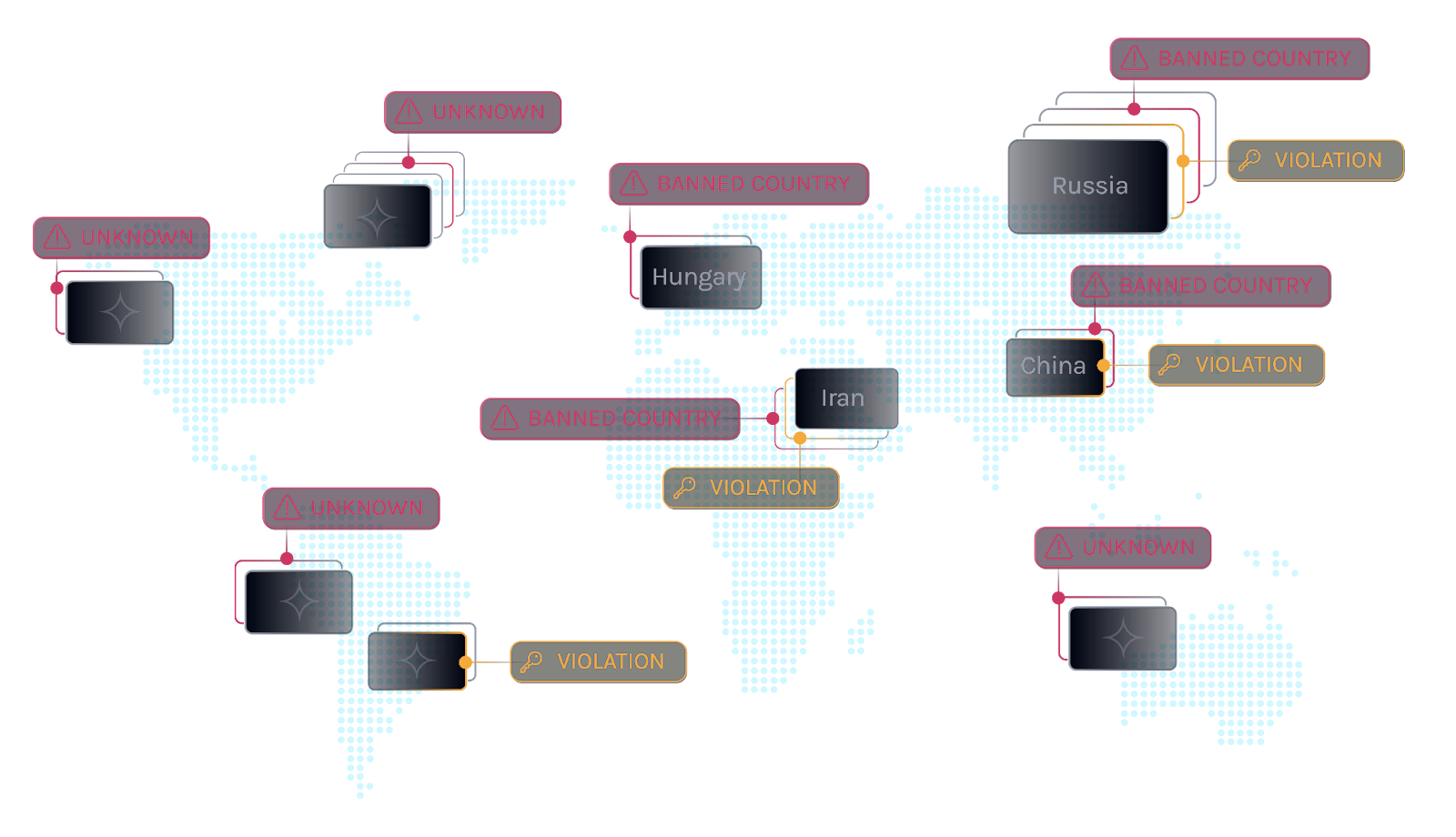
What This Means for Companies Selling to the Government
In practice, government suppliers are heading toward a world where trust must be demonstrated with compliance artifacts, and those artifacts cannot be one-time snapshots.
For most suppliers, this means three things.
- Automated FOCI Risk Identification: An automated and reliable way to identify and assess FOCI risk of open source and third-party components, especially the ones that are quietly included in mission-critical systems.
- Machine-readable Artifact Generation: Continual evidence generation as part of development, not as an afterthought. Security and supply chain assessments that happen only at the end of a release cycle are expensive, slow, and incomplete.
- Secure Sharing: A secure and consistent way to share sensitive supply chain information with government customers without turning every contract renewal into a bespoke compliance scramble.
The uncomfortable reality is that many existing suppliers almost certainly have embedded FOCI exposure today, and they have not been forced to look closely enough to see it.
What This Means for Government Buyers
For acquisition and cybersecurity teams, the burden shifts in a different direction: they must become risk assessors at scale.
That requires:
- Ingesting and analyzing artifacts across thousands of suppliers, not just collecting them.
- Having systems that don’t merely accept attestations, but support verification (consistency checks, provenance, and cross-artifact correlation).
- Establishing continuous monitoring so agencies can rapidly assess impact when new risk emerges, whether it’s a newly compromised package, a maintainer takeover, or a newly identified foreign influence concern.
This is one of the rare moments where both sides are being pulled forward at the same time: suppliers must produce better evidence, and buyers must be prepared to receive, validate, and operationalize it.
AI Makes the Supply Chain Even Murkier
Software supply chain conversations used to revolve around libraries, containers, and build tools. AI adds an entirely new layer. Models, weights, data provenance, and derivative systems.
If software risk can be inherited from a dependency, AI risk can be inherited from a foundation model, especially if the model’s provenance and that of the training data is unclear or adversarially influenced.
The practical implication is simple. Government customers increasingly need to know not just what AI systems do, but where the model came from, what it was trained on, and whether foreign influence can be traced into the pipeline.
Provenance becomes the new perimeter.
The Core Problem: Manual Compliance Cannot Scale
Here is the trap many organizations fall into. Treating supply chain and FOCI risk as an annual compliance effort.
That approach breaks quickly.
The open source ecosystem evolves too fast. Dependencies change daily. Maintainers change. Ownership changes. Trust changes. And your software, especially if it is modern and cloud-based, ships continuously.
If your supply chain process depends on humans chasing PDFs and questionnaires, you are not doing supply chain security. You are doing supply chain theater.
What the moment demands is automation. Continuous monitoring, provenance tracking, evidence generation, and secure sharing built into the software lifecycle.
How Manifest Can Help
Manifest gives you transparency into software and AI you build and buy. Manifest Platform customers work with us to:
- Automatically associate FOCI risk to open source software: Continuously map foreign ownership, control, and influence signals to open source components and third-party dependencies, helping teams understand not just vulnerabilities, but who may be able to influence the software they rely on.
- Automate SBOMs and keep them current: Generate SBOMs in seconds and maintain an always up to date inventory with continuous monitoring and enrichment, so you are audit ready without end of cycle scramble.
- See beyond repo only scanning: Go beyond individual repositories to understand what is actually deployed, including binaries and embedded code, reducing blind spots and incomplete coverage.
- Prioritize real risk, not just CVEs: Assess vulnerabilities with richer context, including exploitability signals and broader supply chain risk indicators, so teams focus on what matters most.
- Operationalize third party risk: Ingest supplier SBOMs in SPDX and CycloneDX formats, normalize them, and use them to streamline third party and supply chain risk reviews at scale.
- Streamline SBOM and VEX exchange with government customers: Request, validate, and track supplier SBOMs and VEX, then share them securely and consistently so assessments and renewals do not turn into one-off compliance drills.
- Meet high assurance government needs: Built for mission critical environments and aligned to high assurance government requirements.
In short, you cannot secure what you cannot see. Manifest helps you see everything, prove it continuously, and share it safely.
Talk to our team of experts and see the Platform in action.


.png)
